Single Sign-On (SSO)
What is SSO?
Single sign-on (SSO) is an authentication process that allows users to sign on to their applications and services with a single set of credentials. SSO is a core capability of identity and access management (IAM) technology that makes it easier for users to have convenient and secure online experiences. In a cloud environment, this is called "cloud SSO."
SSO establishes trust between the identity provider (IdP) and the service provider (SP). The IdP handles the identity information that authenticates the user requesting SSO, and the SP handles the service or application that the user wants to access.
Identity standards such as SAML, OAuth2, and OpenID Connect enable the secure sharing of identity data among multiple SPs and IdPs. Without standards, each connection would require customized development. The following graphic illustrates how SSO streamlines the sign-on process by giving employees secure, one-click access to resources or services from any device.
How does SSO work?
During SSO, an IdP uses an accepted identity standard of communication, such as SAML, to pass an encrypted assertion between the user and the SP. If the user is successfully authenticated through SSO, they have secure, one-click access to a variety of services without the need for repetitive credential entry, multiple passwords, or separate accounts.
SP-initiated federated SSO
To enable SSO, the IdP must implement a centralized authentication server that all apps can use to confirm a user’s identity. This server can validate user identities and identity or access tokens with data that confirm the user’s identity, privileges, and granted authorizations.
The following diagram illustrates the standard steps of SP-initiated federated SSO.
- The user browses to the website or application they want access to (the SP).
- The SP sends a request and redirects the user to the SSO system (the IdP).
- The user is prompted to authenticate by providing credentials.
- The IdP validates the user's credentials.
- The IdP sends an assertion to the SP to confirm authentication.
- The user is granted access to the desired application.
IdP-initiated federated SSO
The following graphic shows the standard steps of IdP-initiated federated SSO.
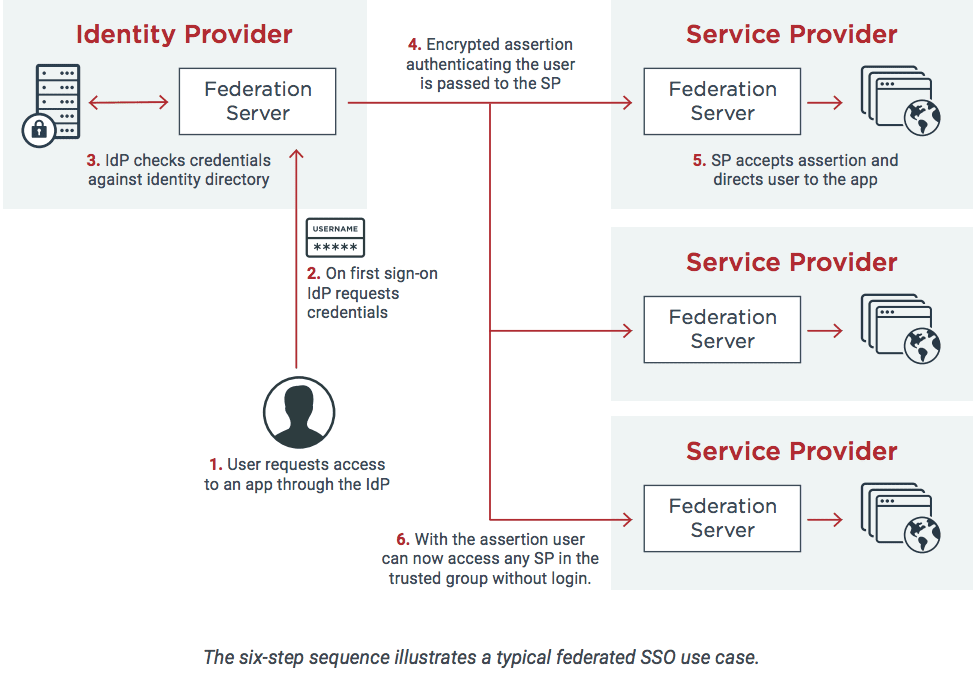
- The user requests access to an app through the IdP.
- On first sign-on, the IdP requests credentials.
- The IdP checks credentials against the identity directory.
- An encrypted assertion authenticating the user is passed to the SP.
- The SP accepts the assertion and directs the user to the app.
- With the assertion, the user can now access any SP in the trusted group without login.
What are the benefits of SSO?
- Stronger security: SSO strengthens enterprise security by reducing the number of passwords that your users have to manage. Because passwords are a popular attack vector, reducing reliance on them also reduces the potential for a breach. Asking your users to only remember one password decreases their tendency for risky password behavior, such as reusing passwords, writing them down, or sharing them with others.
- Enhanced customer experience: SSO eliminates the frustration of juggling multiple passwords and needing to sign on multiple times. Customers can sign on once and easily access all of the products and services that they need. With nearly three out of four customers reporting that experience is an important factor in purchasing decisions, SSO is a great place to start enhancing the customer experience.
- Improved employee productivity: With many enterprises moving to the cloud and adding outside services to their menu of productivity tools, the need for SSO in the workplace is increasing at a rapid pace. SSO is particularly valuable for employees who are remote or use multiple devices to get their work done because SSO enables them to sign on just once each day with one set of credentials.
SSO grants employees easier access to the resources that they need to do their jobs. By granting faster access without sacrificing security, you’re streamlining their work experience, giving them more time to focus on important tasks.
- Lower IT Costs: Decreasing the number of passwords also decreases the number of password-related help desk tickets. Fewer password resets may not sound like a big deal, but organizations spend a lot of money for password-related support costs. By minimizing the number of passwords in use, you can save a lot of money.
Every day, our digital world presents us with more systems and applications to use in our lives. Creating and remembering complex passwords for every app is a challenge and potentially a security risk. By implementing SSO, you can give your customers, employees, and partners the ability to access different applications and services easily, quickly, and securely.
Is SSO right for my organization?
When considering SSO integration, organizations are likely to be looking at a solution that addresses the three main SSO applications. One is increasing security. SSO security is a way to enable Zero Trust principles and ensure a greater level of identity assurance and access authorization. Another is improving user experience. By reducing friction and providing fast and seamless access across a wide array of applications, organizations can boost user satisfaction and productivity. And a third SSO application is to save costs by reducing password reset support calls to the helpdesk.
Related Resources
Single Sign-On Solution
Top Benefits of SSO and Why It's Important for Your Business
How to Choose the Right Single Sign-on (SSO) Solution for your Enterprise
Start Today
Contact Sales
See how Ping can help you deliver secure employee, partner, and customer experiences in a rapidly evolving digital world.