The Open Banking Security Profile defines how Third Party Provider (TPP) applications shall obtain and use OAuth and OpenID Connect tokens in a secure way, suitable for financial transactions. TPP applications will need to obtain tokens from account servicing payment service providers (ASPSPs) to initiate and complete transactions once a user has provided consent and authorized the ASPSP.
As part of the process of obtaining tokens, the security profile defines what authentication methods ASPSPs must support and make available to TPPs to authenticate. The following is required by the security profile:
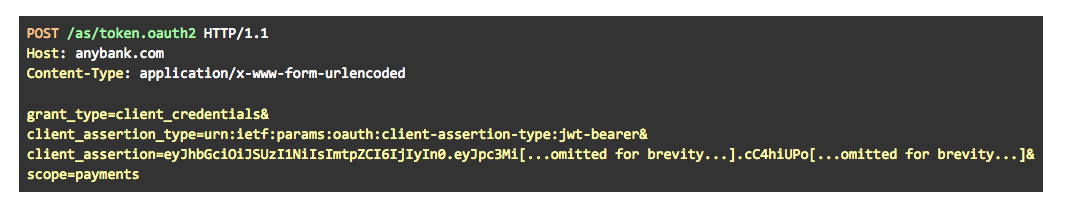
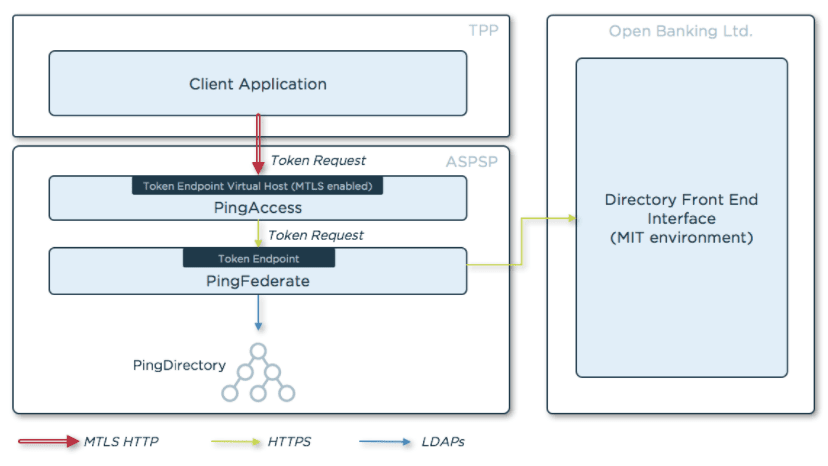
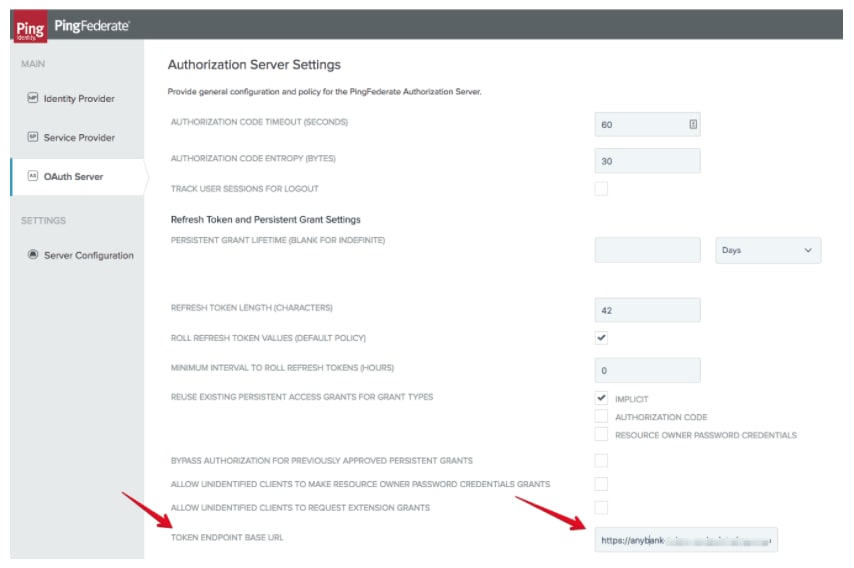
ASPSPs must secure the token endpoint, used by TPPs to obtain tokens, using mutually authenticated TLS.
ASPSPs must make available one of the following methods at the token endpoint:
MTLS as defined in the Mutual TLS Profile for OAuth 2.0 specification.
Client ID and secret over a mutually authenticated channel.
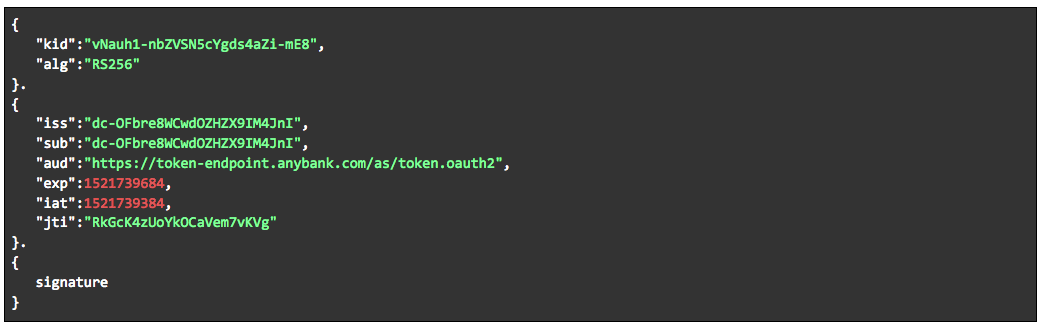
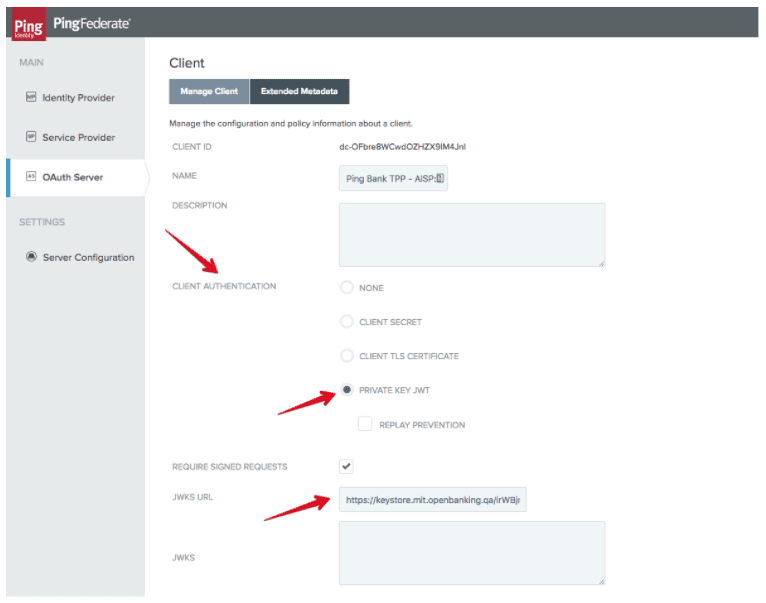
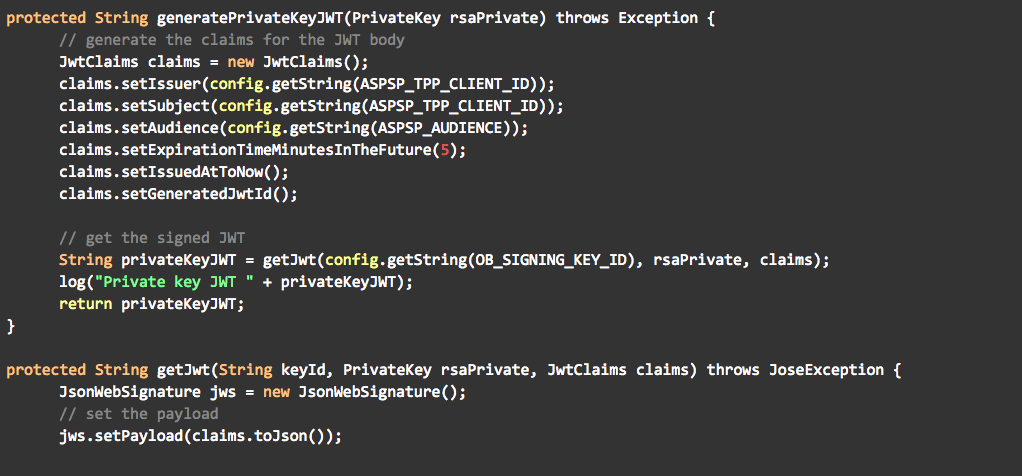
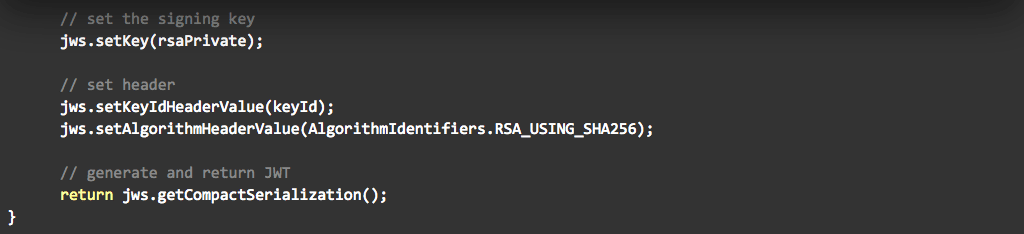
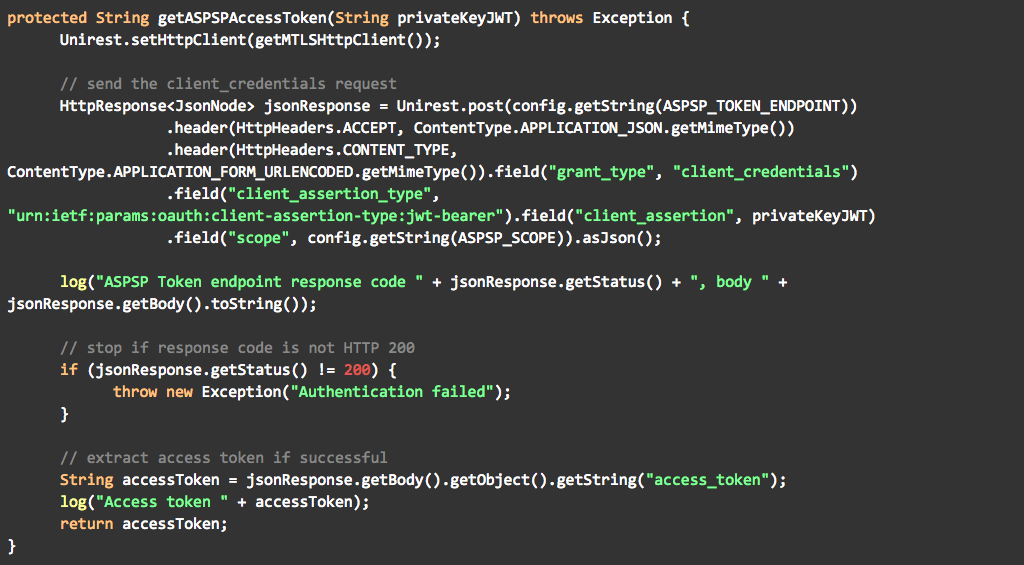
Private Key JWT as defined in the OpenID Connect Core specification.
Of the three methods available, MTLS and Private Key JWT are recommended by Open Banking. In this blog post I will explain how to implement Private Key JWT using the Ping Identity software stack. You can also view my previous blogs on how to enable Open Banking dynamic client registration with Ping Identity and how to use the client registration tool.