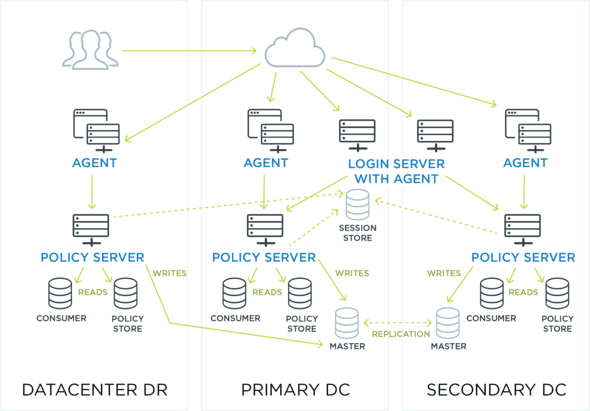
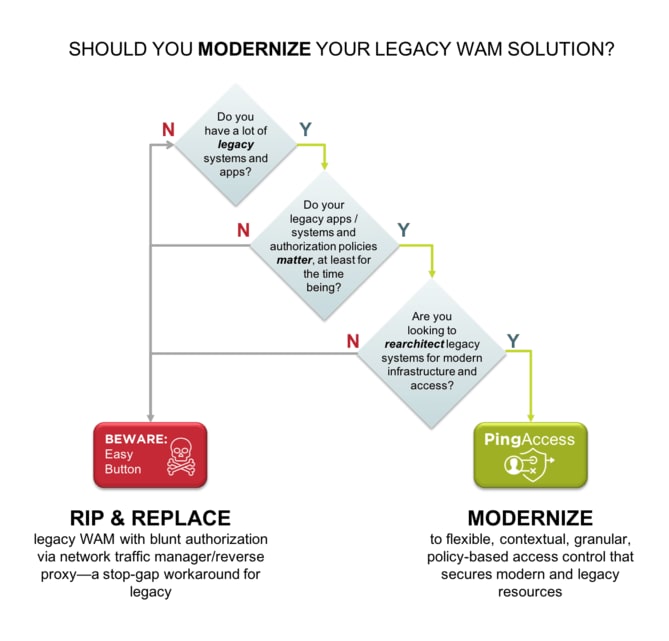
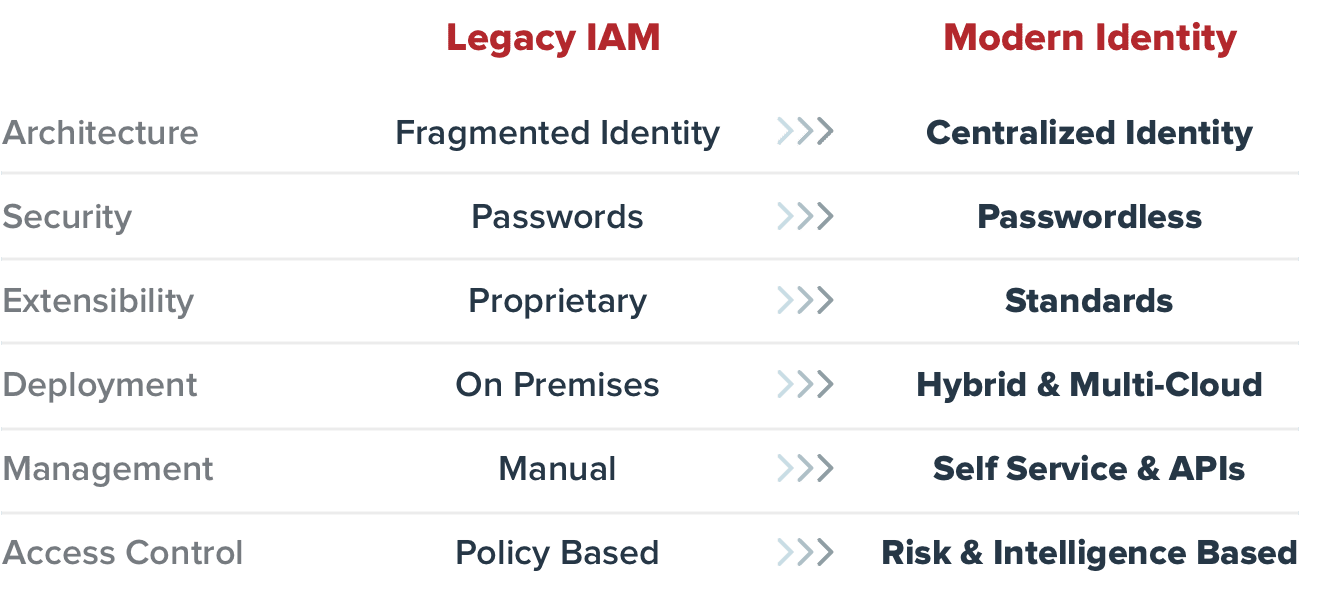
Modern identity and access management (IAM) systems stand out as a comprehensive solution for managing access across diverse application ecosystems, ranging from cloud-based services and SaaS platforms to on-premises software. Unlike legacy web access management (WAM) solutions, IAM is designed to address the dynamic requirements of modern enterprises. These systems provide robust security measures, centralized administration, and unparalleled flexibility, ensuring that businesses can meet evolving security and operational needs.
Enhanced Security
One of the defining features of modern IAM systems is their ability to offer enhanced security through advanced technologies. Multi-factor authentication (MFA) adds an extra layer of protection by requiring users to verify their identity using multiple factors, such as a password, a device, or a biometric identifier. Additionally, risk-based adaptive access continuously evaluates contextual signals—such as device type, geographic location, and login behavior—to determine whether access requests should be granted, flagged, or denied. This real-time evaluation helps prevent unauthorized access by recognizing anomalies that indicate potential security threats.
Centralized Administration
Modern IAM systems simplify the management of access policies and auditing through centralized administration. Unified dashboards enable IT teams to set, monitor, and enforce access controls across the entire organization from a single interface. This centralized approach reduces the complexity of managing disparate systems and enhances visibility into access events, making it easier to identify and address vulnerabilities. By streamlining administrative workflows, IAM solutions save time, improve operational efficiency, and support compliance efforts with evolving regulatory standards.
Flexibility and Scalability
Unlike the rigid frameworks of legacy WAM systems, modern IAM solutions are built with flexibility and scalability in mind. They support dynamic deployment models that cater to hybrid environments, allowing organizations to seamlessly manage access for both on-premises and cloud-based resources. As businesses grow or adopt new technologies, IAM systems can scale to accommodate additional users, devices, and applications without compromising performance or security. This adaptability ensures that organizations remain future-proof, capable of evolving alongside technological advancements and market demands.
Integration with Open Standards
Modern IAM solutions leverage open standards such as OAuth 2.0, OpenID Connect, and SAML to enable secure and seamless authentication. OAuth 2.0, for example, allows third-party applications to access resources on behalf of users without sharing credentials, while OpenID Connect facilitates user authentication and single sign-on (SSO). These protocols not only enhance security but also simplify integration with third-party applications, enabling token-based authentication and supporting the shift toward passwordless workflows. By adopting open standards, IAM solutions ensure compatibility with a wide range of technologies and provide businesses with the flexibility to implement advanced access controls effortlessly.
Modern IAM systems represent a significant leap forward in access management, offering the tools enterprises need to secure their digital ecosystems while improving efficiency and user experience.