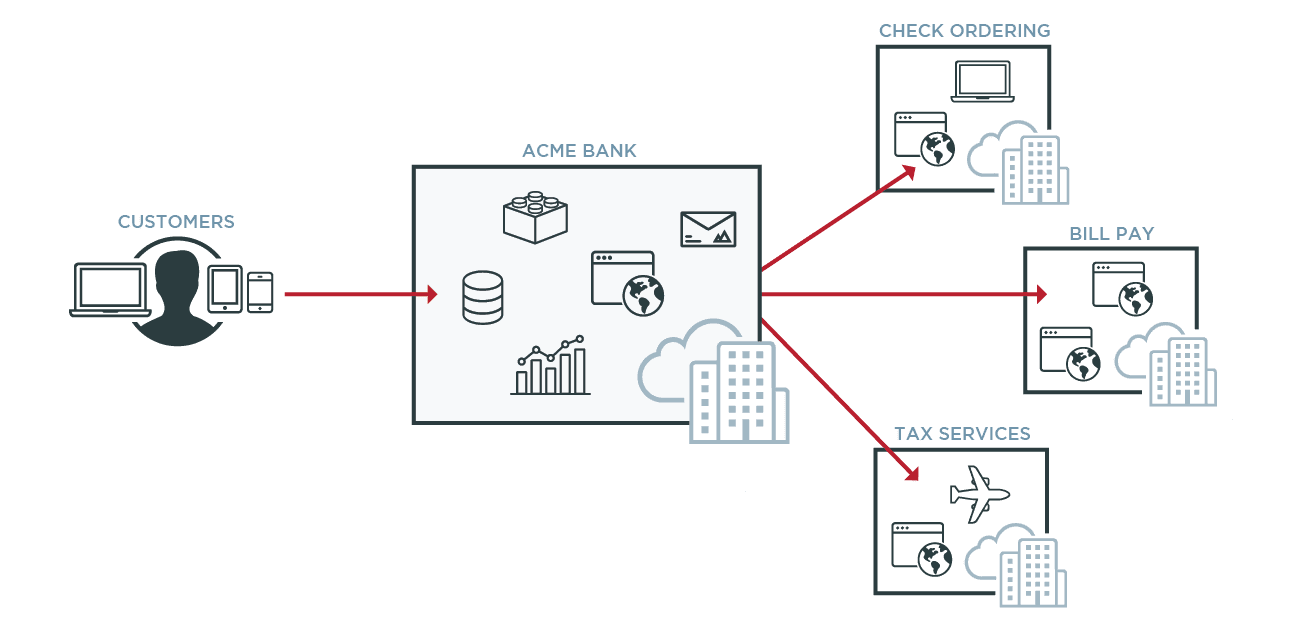
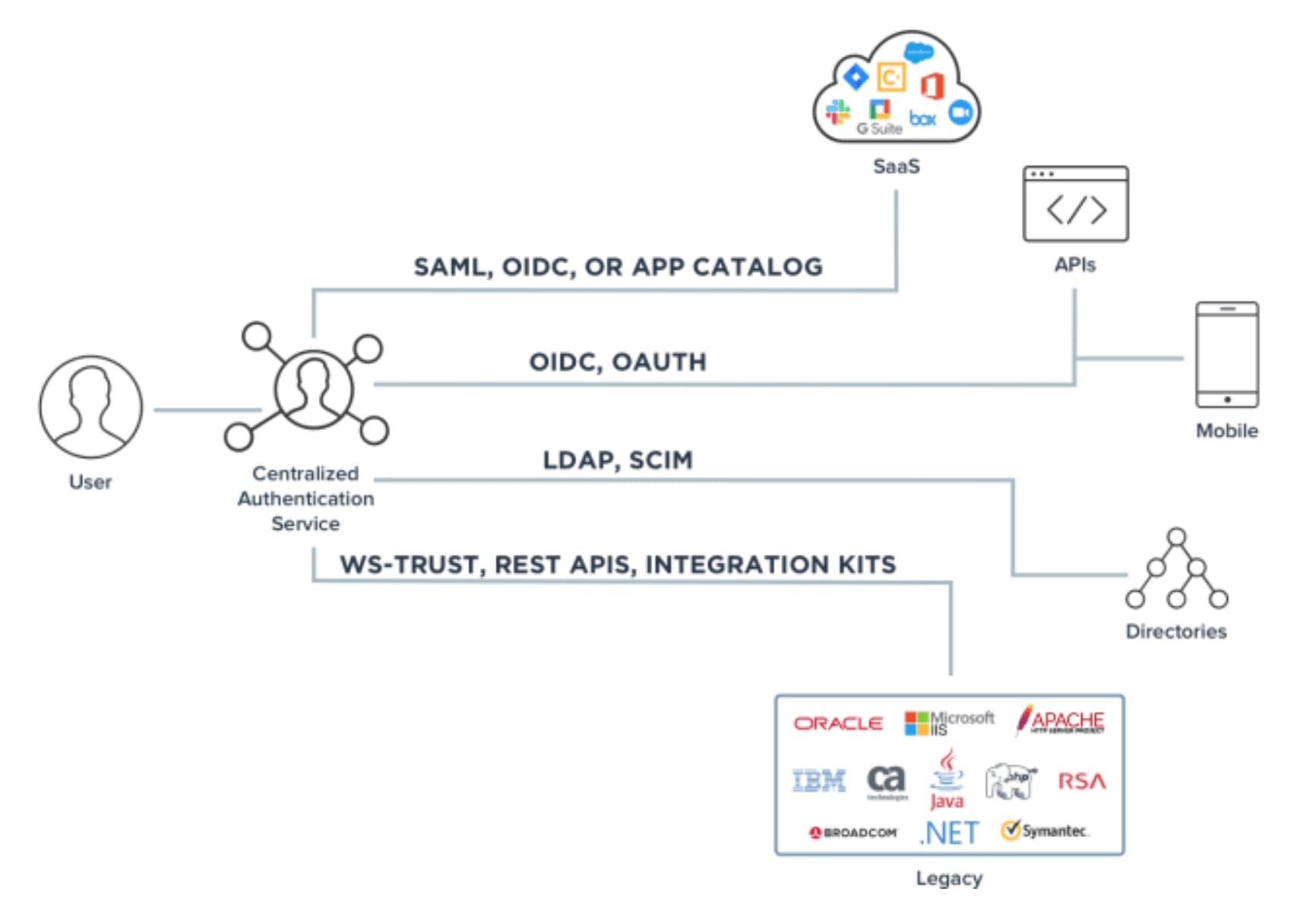
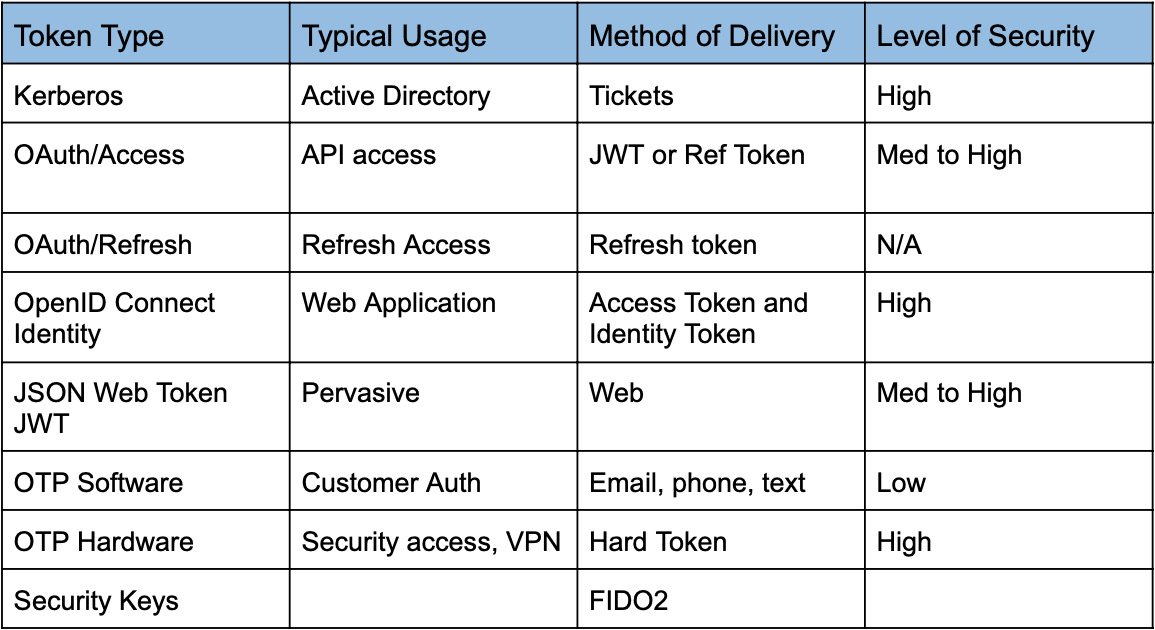
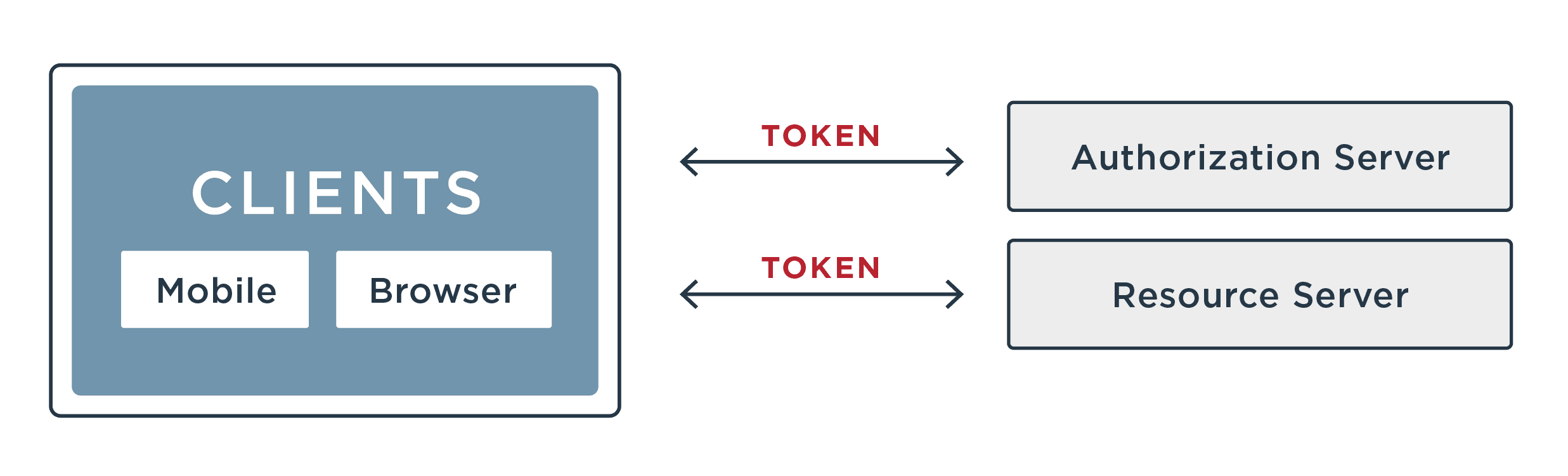
Identity management topics can be a bit abstract or in the clouds, literally. At its core, authentication is a method for verifying that a user is who they claim to be, and used to keep bad actors out of your network. Unlike passwords, which can be easily compromised and used by hackers for data breaches, tokens are more secure.
Key Takeaways
- Tokens as Digital Keys – Tokens replace passwords for authentication, acting like secret phrases or knocks in movies to verify identity securely.
- How Token-Based Authentication Works – A secure token is exchanged instead of credentials, with types including access tokens, ID tokens, refresh tokens, self-signed tokens, and bearer tokens.
- Security Advantages – Token-based authentication is stateless, self-contained, and provides fine-grained access control, making it more secure than traditional password-based systems..
- Authentication Protocols – Common frameworks include OAuth 2.0 (third-party authorization), OpenID Connect (modern web apps), SAML (SSO for web apps), and CIBA (no browser redirects).
- Enhancing Multi-Factor Authentication (MFA) – Tokens improve security in MFA by using hard tokens (key fobs, dongles) and soft tokens (software-based OTPs, biometrics).
86% of data breaches involve the use of stolen credentials.
Read on to learn:
- What a token is
- Why tokens should be used
- What token-based authentication is and how it works
- The benefits of token-based authentication
- Types of authentication protocols, including uses and limitations