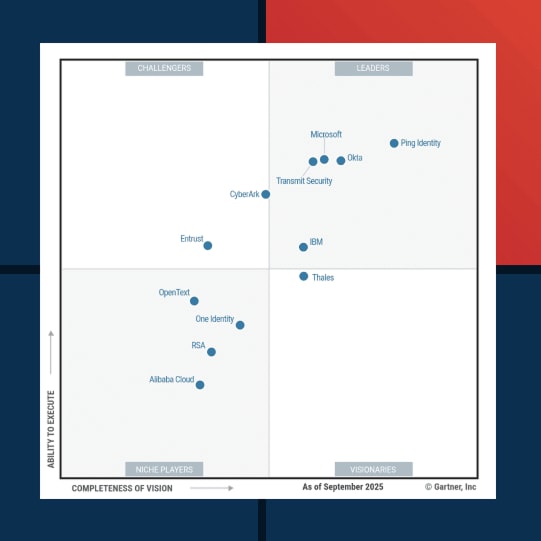
2025 Gartner® Magic Quadrant™ for Access Management
For the ninth year in a row, Ping Identity has been named a Leader. We believe our upper-right placement this year reflects what global enterprises already know—when it comes to scaling secure, seamless digital experiences, Ping delivers.
We Scale with You.
Proven across the most complex hybrid, multi-cloud, and third-party environments.
We’re Built for What’s Next.
AI-ready identity for leaders who are navigating the future of access.
We’re Flexible Without Compromise.
Standards-based, and built to work with the tech you already use.
Whether you need to modernize identity, secure every access point, or enable agility across your organization, choosing a partner just got a lot easier.
This comprehensive report provides the insights from Gartner on access management technologies, vendor Strengths and Cautions, and why we believe recognized solutions can drive your organization's security strategy forward.
Gartner, Magic Quadrant for Access Management, Brian Guthrie, Nathan Harris, Steve Wessels, Yemi Davies, 11 November 2025
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally, and MAGIC QUADRANT is a registered trademark of Gartner, Inc. and/or its affiliates and are used herein with permission. All rights reserved.
This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from Ping Identity.