There are many positives to working in the CTO group at Ping - including working on interesting projects, continuous opportunities to learn, and friendly and intelligent colleagues.
Alas, none of those criteria apply to the email thread below with John Bradley discussing Proof of Possession (PoP) models for protecting OAuth exchanges.
As background, 'proof of possession' refers to crypto mechanisms that mitigate the risk of security tokens being stolen and used by an attacker. In contrast to 'bearer' tokens, where mere possession of the token allows the attacker to use it, a PoP token cannot be so easily used - the attacker must have both the token itself and access to some key associated with the token (which is why they are sometimes referred to 'Holder of Key' (HoK) tokens).
PoP describes a general security characteristic of a token - there are different ways to achieve that characteristic. The thread below teases out some of the pros and cons associated with those different models.
Relevant links:
- Token Binding spec collection
- Links to specs on Token Binding for various token types
After taking a deep breath (because I know what typically happens when I pose technical questions to John) I start the thread by asking:

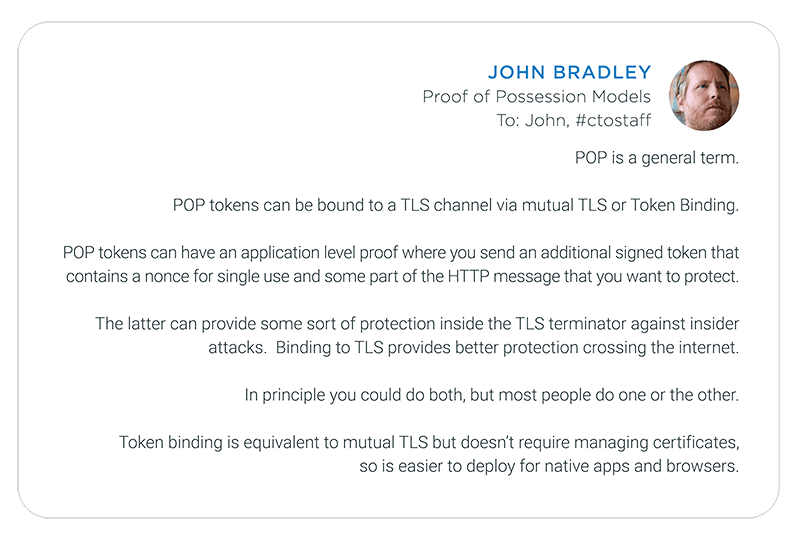
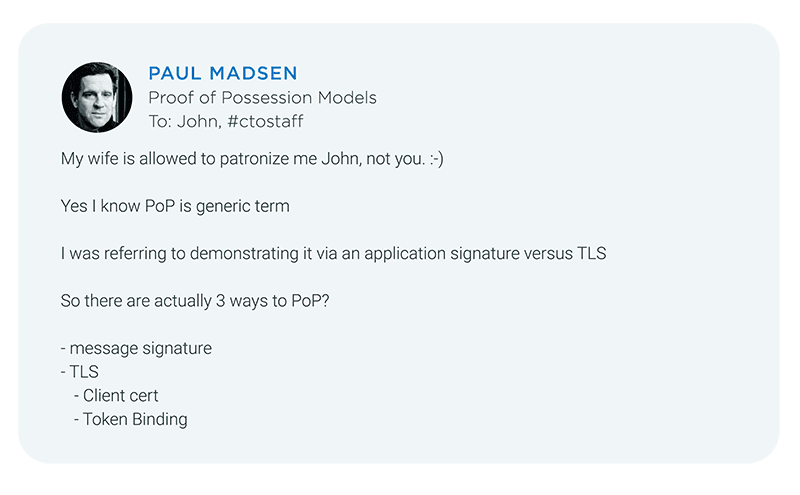
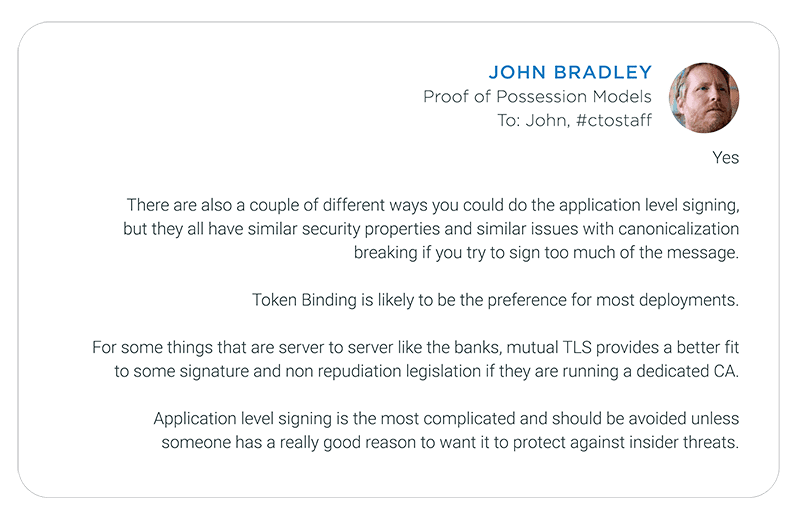

Proof of Possession models and specifications will almost certainly be a topic of discussion at the upcoming Cloud Identity Summit June 19-22 in Chicago (though John and I may not end up on stage at the same time). We hope to see you there.