PingOne Protect
Tour the Product
But constant prompts for every transaction can feel like hitting a red light at every Intersection.
Plus, with the evolving sophistication of hacks, You can't always trust that MFA only allows legitimate users in.
That's where PingOne Protect comes in.
PingOne Protect leverages network, device, and behavioral signals to detect non-human and high Risk activity.
That way, you can catch account takeover and new Account fraud in real time.
Plus, by identifying low-risk, legitimate users, you ensure that they have a secure and Delightful experience without being unnecessarily interrupted.
That means fewer abandoned carts for you and less frustration for your customers.
Give your users the convenience they crave with the security they need.
Experience a better experience with PingOne Protect.
Meet PingOne Protect
Prevent account takeover, new account fraud, and MFA fatigue with PingOne Protect. By evaluating multiple attack vectors, assigning risk scores, and providing insights, PingOne Protect triggers mitigation tools to block attacks and allow legitimate users to authenticate easily.
How it Works
PingOne Protect’s intelligence-based policies combine the results of multiple risk predictors to calculate an overall risk score. The score correlates to policies that determine the type and amount of friction to introduce into the user flow, such as CAPTCHA, password resets, selfie verification, and push notifications. Optimize scores for each predictor, aggregate predictors, add signals from third parties, and create overrides.
Predictors include bot detection, IP velocity, user velocity, geovelocity anomaly, user location anomaly, IP reputation, anonymous network, user risk behavior, user-based risk model, new device detection, suspicious device detection, custom/third-party predictors, and composite predictors.
With PingOne Protect, you can:
Reduce the number of times legitimate users are interrupted
Prevent identity fraud by evaluating activity and detecting anomalies
Gain visibility into risk and fraud posture and trends
User Journey Alignment
PingOne Protect spans all stages of the user journey.
Stop Account Takeover and New Account Fraud
Bad actors gain access and do harm by attacking surfaces like registration forms, login, account recovery, and password reset. PingOne Protect detects attack vectors specific to account takeover and new account fraud, such as bots, emulators, brute force, credential stuffing, tampered devices, password spraying, etc.
Address MFA Fatigue
Whether it's your customers abandoning carts or your employees losing productivity, login friction hurts your business. Reduce login friction by using real-time risk scores to make intelligent authentication decisions. Pair PingOne Protect with any mitigation service like PingOne MFA or PingID to improve user experience.
Detect Bots
Bad actors use software that performs task automation (bots) to scale their attacks. By leveraging network, device, and behavioral signals - any non-human attempt to login or register/modify an account is detected immediately.
Recognizing abnormal user behavior can help your organization detect malicious activity, but this requires analyzing vast amounts of authentication data to learn behavior patterns. PingOne Protect applies learning and training capabilities to User and Entity Behavior Analytics (UEBA) in real-time, continuously evaluating unusual behavior compared to the user's past behavior.
Get Started on Your Passwordless Journey
Pairing sign-on and authentication with detection techniques improves security and makes registration/login adaptive and flexible. With continuous risk evaluation happening in the background, users experience minimal interruption. Second-factor authentication, like QR codes, magic links, and biometrics, is triggered only when necessary.
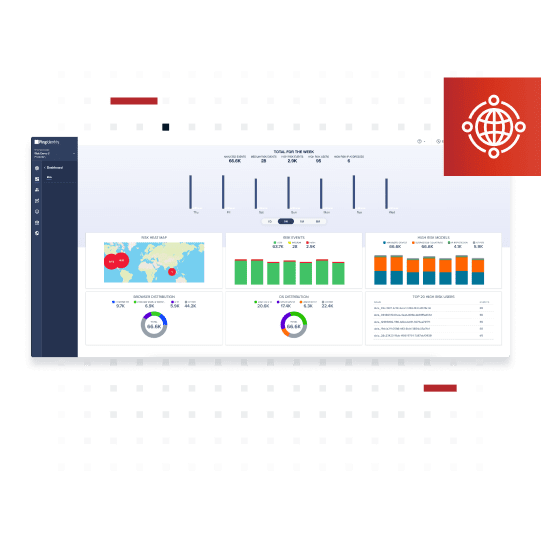
Insights into Risk and Fraud
Understanding where risk lies can help you make authentication decisions that increase security posture. PingOne Protect has robust dashboards and reports that provide insight into risk events, high-risk locations and factors, the riskiest users, and browser and operating systems distribution. Deep dive into risk data by inspecting monitored user activity using advanced filtering options.
Benefits & Features
Quickly identify high-risk users in real-time and force mitigation
Allow low-risk users access without forcing unnecessary mitigation
Leverage risk signals for adaptive authentication
Apply dynamic learning and training capabilities to user behavior
Ingest custom or third-party risk signals
Deep dive into risk with reports and dashboards
Aggregate risk scores, create composite predictors, and apply overrides
Differentiate between normal and abnormal authentication requests
Integrates with PingFederate and all PingOne products, including DaVinci
Visibility into activity and events throughout the user journey
Business Value
Prevent fraud
Minimize friction
in the user
experience
Minimize risk
Flexible Deployment Options
PingOne Protect can be deployed as:
PingOne Services - Multi-tenant SaaS
Platform Alignment
PingOne Protect is an integral part of the PingOne Cloud Platform and is essential to all identity and access management user journey phases.
Start Today
Contact Sales
See how Ping can help you deliver secure employee, partner, and customer experiences in a rapidly evolving digital world.