[MUSIC] Hey, welcome to this fast chat exploring why zero trust starts with identity.
I'm Black Hat contributing editor Alex Wawro and with us today is Baber Amin, CTO west for Ping Identity.
Baber, thanks for joining us.
>> Thank you, Alex.
>> All right, let's get right into it.
I think first let's ask like what are the essential components of zero trust?
And why is identity key?
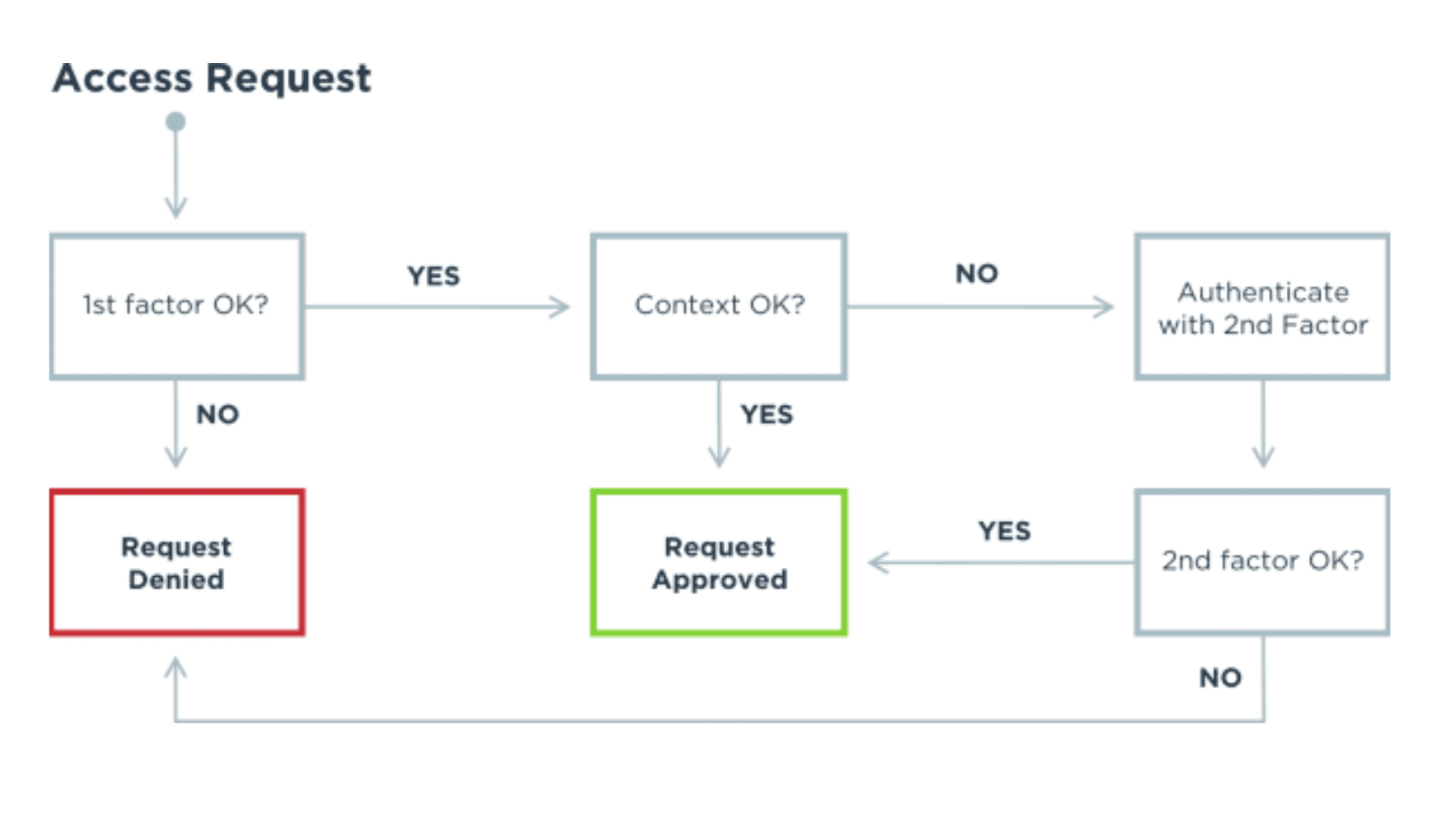
>> So, well the one essential component of zero trust is identification right?
If you don't know who somebody else is, then, you're you're starting off on the wrong foot.
And that's one of the reasons why identity is key.
Because you're not relying on any discrete events anymore.
You're not relying on any discrete mechanisms, but it's more of continuously verifying and and evaluating trust in the person or the device or the process.
>> So what are some easy wins for people who are looking to get started with zero trust?
>> So we get asked that a lot, right and I always tell people look, again start with proofing, so making sure that who it is from before you give somebody a credential and then move to authentication.
Then move to access and then move to consolidating your data stores.
Like a lot of people think, let me just consolidate my data stores.
And you know that project takes forever and it never succeeds because it never finishes.
>> Yeah.
So what type of companies do you think would benefit most from a zero trust approach?
>> Well, I used to say that you know, if you have a lot of people that are remote workers, they would benefit the most.
But given that everybody is remote now, I say everybody can benefit, because without zero trust, which is really a bad name for this, right?
Because it's not like you don't trust anything it's that you don't trust anything by default, right in a static manner, so a better name would be maybe ephemeral trust or something like that.
But everybody benefits from that, especially nowadays when you have all folks working remotely in giving things like telehealth or even the proofing that a doctor can prescribe you medicine they have to go through a certain amount of proofing.
That they are credentialed and everything else so that that used to be all in person, new employees.
Right?
>> Right.
>> When you get a new employee on board, you check their authorization to work the I9 form all of that, that used to be in person.
So all of that has to be remote now too, so pretty much everybody benefits from implementing zero trust principles.
>> So, besides technologies like what are the key things people need to know about the people and processes required for zero trust?
>> Yes.
So that's another place where people think that zero trust is some silver bullet and if I implement these four things, and yay, I'm good to go.
[LAUGH] But security is a people problem and a people solution.
The worst thing in security and the biggest hole in security is the combination of the person, email and clicking on links.
Because that violates no matter what kind of firewalls you put up no matter what kind of gates you put up.
It's that one person who didn't think about it or just clicked on it, right?
So that's the weakest link.
So processes become very important because it's educating your folks.
Look, don't do this or, don't connect to systems, don't download information to your machine that is not a possibly have the same level of security or patches on it right?
Don't download super secret documents to grandma's PC that has never been patched for the last 10 years.
And just because you need to work on something right after Thanksgiving dinner.
That is if we get to go to grandma's house this year.
So, yeah, people, processes, education and in really getting that buy in from your organization is very, very important.
>> Yeah, that makes a lot of sense.
Well Baber, thank you so much for joining us today and thanks everyone for taking part.
>> Thank you, Alex.
[MUSIC]