FRAUD PREVENTION
Prevent Fraud in
Real Time
Detect and stop AI-driven attacks before they hit your customers, employees, and partners.
We work with the world’s top brands
THE CHALLENGE
Fraud Evolves Fast. So Should You.
Deepfakes &
AI-Driven Threats
Fraudsters now use deepfakes, synthetic identities, and AI bots to slip through traditional defenses. We detect and stop them in their tracks, in real time—before they do damage.
Account-Based
Fraud
Bad actors use fake IDs, stolen credentials, and social engineering for new account fraud (NAF) and account takeovers (ATO). We help you spot and stop them before it hits your bottom line.
Prevention Without Unnecessary Friction
Security shouldn’t kill your user experience (UX). Our adaptive approach lets trusted users move effortlessly, and safeguards only step in when something looks suspicious.
THE CHALLENGE
Fraud Evolves Fast. So Should You.
Deepfakes & AI-Driven Threats
Fraudsters now use deepfakes, synthetic identities, and AI bots to slip through traditional defenses. We detect and stop them in their tracks, in real time—before they do damage.
Account-Based Fraud
Bad actors use fake IDs, stolen credentials, and social engineering for new account fraud (NAF) and account takeovers (ATO). We help you spot and stop them before it hits your bottom line.
Prevention Without Unnecessary Friction
Security shouldn’t kill your user experience (UX). Our adaptive approach lets trusted users move effortlessly, and safeguards only step in when something looks suspicious.
THE SOLUTION
Fight Fraud Smarter,
Not Harder
Our fraud prevention solutions put you in control with proactive threat prevention, detection, and response. Using AI-driven insights, identity verification, risk-based authentication, and more, you can make sure the fraudsters never compromise your user experience—or trust.
Here’s how it works:
Real-Time Threat Detection: Instantly identify and neutralize threats as they happen.
Deepfake Defense: Easily spot and stop AI-based attacks before they cause harm.
Enhanced Identity Verification: Verify real users without adding unnecessary friction.
Risk-Based Authentication: Authenticate trusted users based on context and behavior.
Advanced Fraud Prevention,
Made Simple
Combating advanced fraud takes an integrated prevention approach. Here are our core capabilities that arm your organization against the threats of today—and tomorrow:
Advanced Fraud Prevention, Made Simple
Combating advanced fraud takes an integrated prevention approach. Here are our core capabilities that arm your organization against the threats of today—and tomorrow:
Instantly flag anomalies and distinguish trusted users from fraudsters in real time.
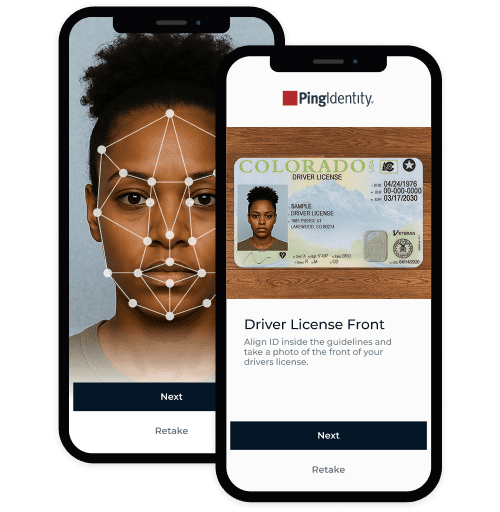
Use biometrics and verified documents to stop deepfakes and synthetic identities—with minimal disruption.
Trigger step-up authentication only when something’s off, and keep low-risk users flowing.
Evaluate bot integrity in real time, and block malicious bots and compromised AI agents.
Respond to threats instantly with automated actions. Keep losses and disruption to a minimum.
DIVE INTO THE DETAILS
Fraudsters are getting smarter, and we’re here to help you outsmart them. Here’s how we identify threats in real time, secure your legitimate users, and build trust in your digital experience.
Don’t Just Take Our Word for It
Don’t Just Take Our Word for It
Image Carousel
Real-Time Prevention. Real-World Results.
Our trusted, unified platform already protects millions of users globally. With unmatched security, scalability, and simplicity, we don’t just help you stop fraud. We help you outsmart it.
Helpful Resources
Helpful Resources
Frequently Asked Questions
When it comes to protecting your organization from fraud, you need more than just a quick fix—you need a partner you can trust. Curious about what sets us apart? We’ve got clear answers to common questions.
Our platform leverages risk scoring and machine learning to analyze multiple signals throughout sessions including user behavior, device data, and transaction patterns. Our orchestration capabilities allow you to design user journeys where suspicious activity will trigger immediate mitigation, keeping both users and your business secure.
Not at all. Our adaptive MFA ensures additional challenges only occur for high-risk users, while legitimate users enjoy a quick, seamless experience. In fact, low-risk users should see less friction and a more streamlined experience.
Yes. Our solution fully aligns with major compliance regulations, ensuring secure and responsible data handling and user privacy.
Absolutely. Our platform seamlessly integrates with your current workflows and security infrastructure.
Yes. Our solution proactively detects deepfake and synthetic identity fraud using sophisticated identity proofing technology.
We continuously analyze signals such as device posture, location, network reputation, and user behavior. Our orchestration capabilities allow you to automate mitigation in situations where risky activity is detected, requiring step-up authentication, limiting access, or blocking suspicious actions in real time.
Gartner and Peer Insights™ are trademarks of Gartner, Inc. and/or its affiliates. All rights reserved. Gartner Peer Insights content consists of the opinions of individual end users based on their own experiences, and should not be construed as statements of fact, nor do they represent the views of Gartner or its affiliates. Gartner does not endorse any vendor, product or service depicted in this content nor makes any warranties, expressed or implied, with respect to this content, about its accuracy or completeness, including any warranties of merchantability or fitness for a particular purpose.