DECENTRALIZED IDENTITY
Decentralized Identity = Digital Trust
Give your users control with reusable, verified credentials that reduce fraud, boost privacy, and simplify compliance.
Decentralized Identity = Digital Trust
Give your users control with reusable, verified credentials that reduce fraud, boost privacy, and simplify compliance.
We work with the world’s top brands
THE CHALLENGE
Traditional Identity Falls Short
Fraudsters Are
Getting Smarter
Static credentials and siloed systems are easy targets. Cryptographically secured credentials help you verify, authenticate, and authorize users and block imposters, deepfakes, and ATO.
Users Want
Control
Today’s users expect privacy, transparency, and control of their own data. With verifiable credentials, they decide what to share, with whom, and for how long.
Compliance Is
Complex & Costly
Keeping up with regulations like GDPR, eIDAS, ISO, and KYC isn’t easy. Decentralized identity minimizes the sensitive data you store, audit, and protect, so you can reduce risk and cost.
THE CHALLENGE
Traditional Identity Falls Short
Fraudsters Are Getting Smarter
Static credentials and siloed systems are easy targets. Cryptographically secured credentials help you verify, authenticate, and authorize users and block imposters, deepfakes, and ATO.
Users Want Control
Today’s users expect privacy, transparency, and control of their own data. With verifiable credentials, they decide what to share, with whom, and for how long.
Compliance Is Complex & Costly
Keeping up with regulations like GDPR, eIDAS, ISO, and KYC isn’t easy. Decentralized identity minimizes the sensitive data you store, audit, and protect, so you can reduce risk and cost.
THE SOLUTION
More User Control.
Less Enterprise Risk.
PingOne Neo delivers trusted, user-controlled credentials that are verified and ready for any app or service. A big boost in interoperability that means less friction for them and less risk for you.
Here’s how it works:
Request: The user qualifies to receive a verifiable credential from a trusted issuer.
Create: The issuer verifies the information provided and delivers cryptographically signed credentials in seconds.
Store: The credentials live in the user’s digital wallet—secure and ready to be shared.
Present: The user shares only the data that’s needed for the interaction, nothing more.
Sign: The wallet signs the transaction and approval details by using an advanced electronic signature in the form of a wallet-issued credential that can be shared with stakeholders.
How to Go from
Centralized to Decentralized
Leverage capabilities that put people and privacy first. Here’s how
we deliver secure, user-centric experiences that give users control
and keep your organization safe:
How to Go from Centralized to Decentralized
Leverage capabilities that put people and privacy first. Here’s how we deliver secure, user-centric experiences that give users control and keep your organization safe:
Use biometric options like selfie matching with liveness detection and government-issued ID to verify identities with confidence.
Create, issue, revoke, and verify internal or trusted third-party credentials—and validate only the data you need, straight from the source.
Ensure users are who they say they are. Stop AI-driven threats like deepfakes, synthetic IDs, and ATO before they start.
Let users control their data and share only what’s essential. Limit what you store to reduce risk and simplify compliance at every step.
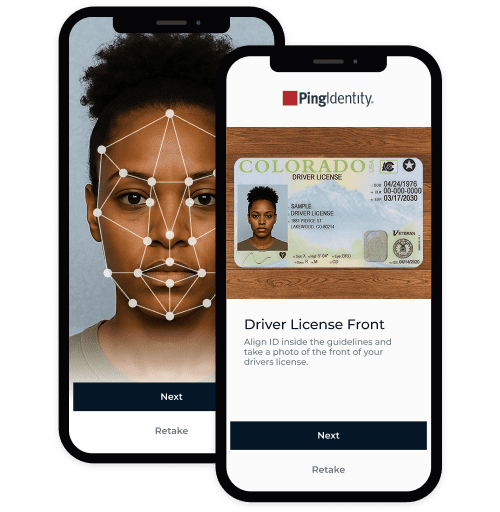
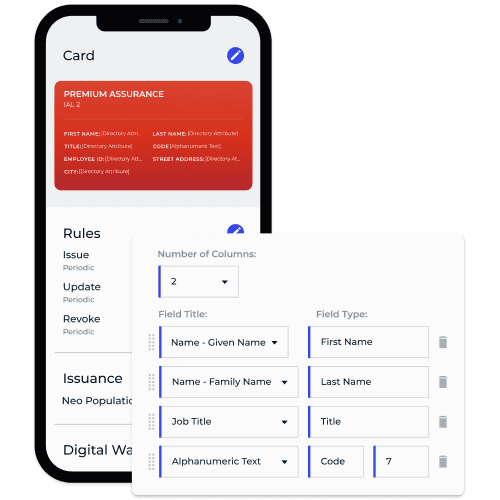
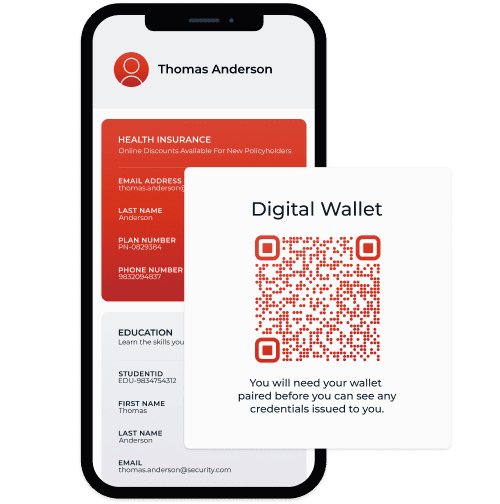
DIVE INTO THE DETAILS
When it comes to securing your digital ecosystem, not all decentralized identity solutions are created equal. It’s not just about protecting your organization and giving your users control over their identity data. It’s about doing it in a way that’s smart, seamless, and scalable.
Don’t Just Take Our Word for It
Don’t Just Take Our Word for It
Image Carousel
Say Hello to Privacy-First Digital Moments
Decentralized identity isn’t just a new approach—it’s a smarter one. Move beyond legacy IAM limitations like static logins and central databases. Give users verifiable credentials they can trust.
Helpful Resources
Helpful Resources
Frequently Asked Questions
Got questions? We've got clear answers to common questions about decentralized identity to get you started.
A new approach where users verify their digital identity and data, store a verifiable record of that personal data in their mobile wallet or a trusted app, and then share that data with third parties.
When you combine identity verification and verifiable credentials with a digital wallet and identity orchestration, you have a comprehensive decentralized identity solution—PingOne Neo.
It removes identity silos and enables users to carry verified credentials across systems and providers, putting users in control of their own data.
Yes. Verifiable credentials are cryptographically signed, tamper-proof, and stored with the user, not in a central repository.
By digitizing user verification, enabling credential issuance and management, and leveraging reusable verified identity, organizations can significantly cut down on verification and operational expenses while increasing security.
Absolutely. Decentralized identity aligns with the following regulations:
- eIDAS & NIST 800: Digital identity, authentication, and trust compliance.
- ISO 27001 & SOC: Security, privacy, and risk management certifications.
- JWT VC & W3C VCs: Verifiable credentials and decentralized identity standards.
- ISO 18013-7: Mobile and digital driver license compliance.
- OIDC4VP, OPENID4VCI, & SIOPv2: OpenID and machine-readable document verification.
Yes. Our standards-based architecture ensures compatibility with your current identity environment.
Gartner and Peer Insights™ are trademarks of Gartner, Inc. and/or its affiliates. All rights reserved. Gartner Peer Insights content consists of the opinions of individual end users based on their own experiences, and should not be construed as statements of fact, nor do they represent the views of Gartner or its affiliates. Gartner does not endorse any vendor, product or service depicted in this content nor makes any warranties, expressed or implied, with respect to this content, about its accuracy or completeness, including any warranties of merchantability or fitness for a particular purpose.