Ultimate Guide to Identity
Defined Security
Table of Contents
Introduction
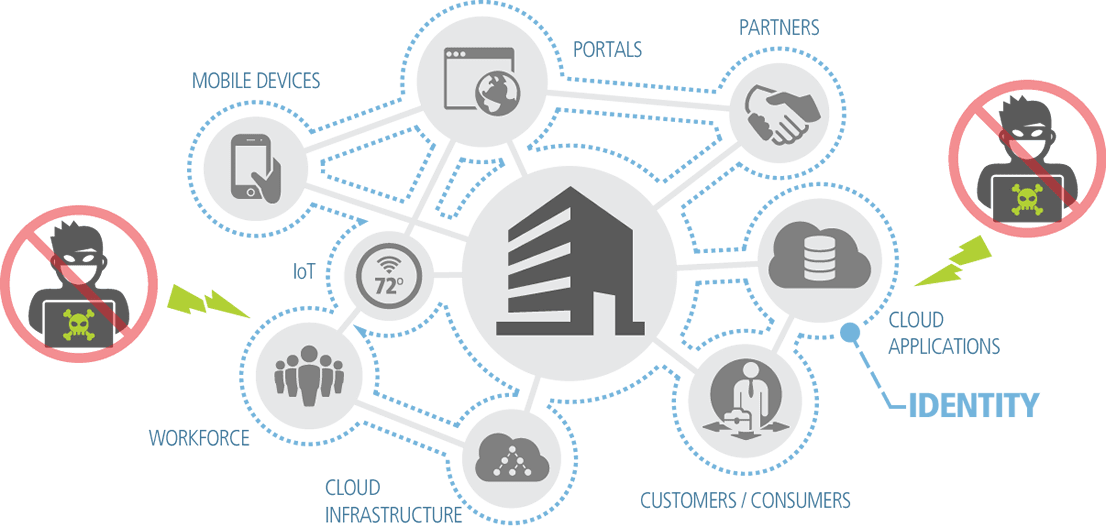
We no longer live in a world where security is defined by a brick-and-mortar office that’s protected by a firewall. Users have moved beyond the confines of traditional security, accessing both internal and cloud applications and data, from multiple devices and locations.
To ensure trusted and secure interactions in this new world, enterprises must embrace security with identity at its core. Through Identity Defined Security, enterprises can move beyond the aging firewall perimeter to keep the bad guys out. Instead, by enabling the right people access to the right things, identity is the new perimeter. Enterprises can empower their workforce, partners and customers with a fluid and secure experience, on any device and from anywhere.
Chapter 1
Start Today
See how Ping can help you deliver secure employee and customer experiences in a rapidly evolving digital world.
Request a free demo
Thank you! Keep an eye on your inbox. We’ll be in touch soon.